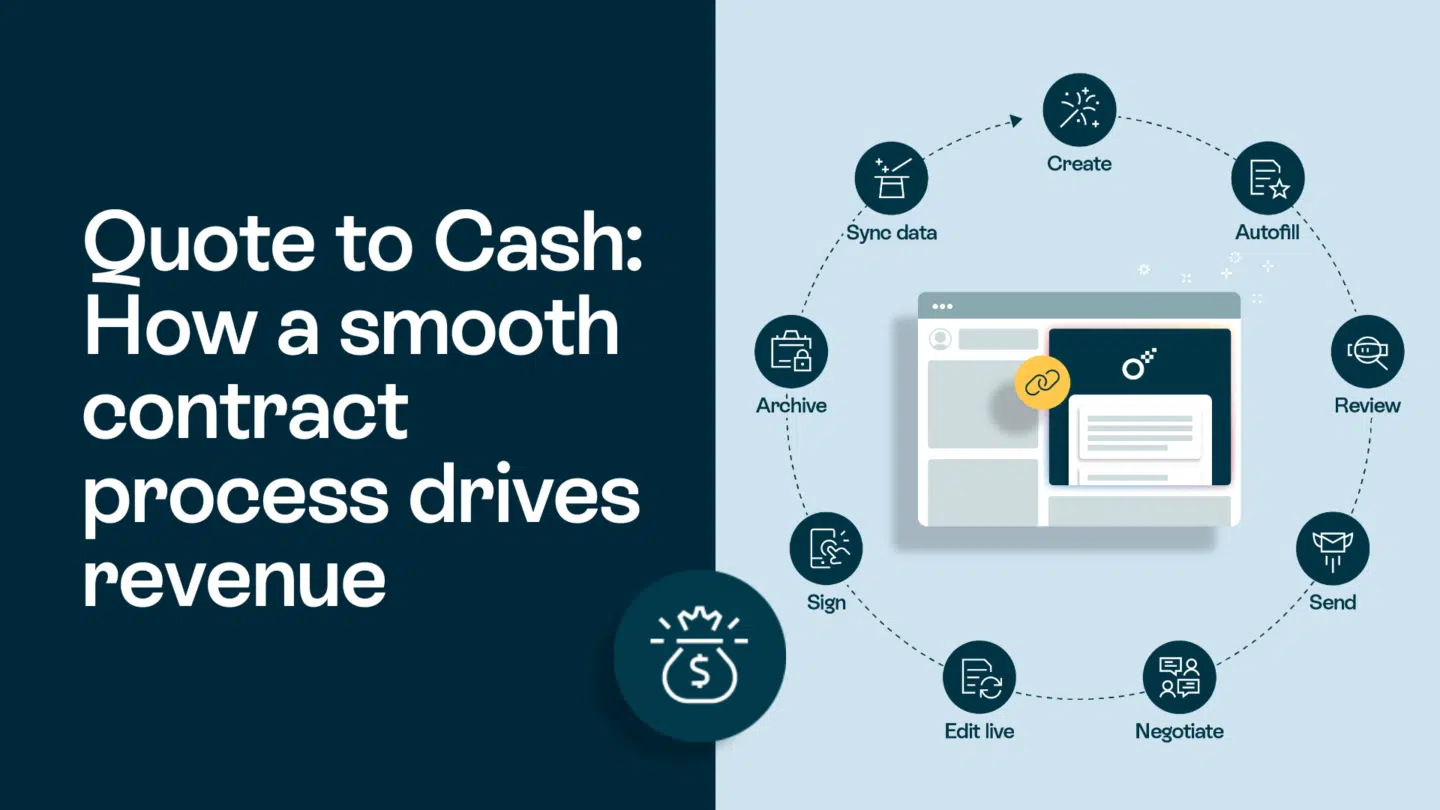
Everyone knows the importance of user permissions and the security they can provide. But what is often overlooked is how having user permissions be customizable to your organizational structure is half of what helps them provide that security. Without it, you’re stuck with user permissions that cause bottlenecks or security breaches.
So why are they so important?
Risk mitigation and security
Limiting access to sensitive data and critical processes is fundamental to mitigating risks. Allowing unrestricted access to numerous individuals increases the likelihood of unauthorized access and potential breaches. By employing user permissions, organizations can restrict access to only those individuals who genuinely require it to perform their duties effectively. This not only safeguards sensitive information but also bolsters the organization’s overall security posture.
Customization and flexibility
Every organization has unique requirements and workflows. A one-size-fits-all approach to user permissions is inadequate in addressing these diverse needs. With customizable access rights, organizations can tailor permissions to match their specific requirements. This flexibility enables them to assign different administrative tasks to various team members based on their roles and responsibilities. Consequently, organizations can maintain granular control over their document management systems, ensuring that each user has precisely the level of access necessary for their duties.
Streamlined workflows
Granting specific admin tasks to designated team members streamlines workflows and enhances operational efficiency. Rather than relying on a single individual to handle all administrative functions, organizations can distribute responsibilities among multiple team members. This not only reduces the risk of bottlenecks but also ensures that administrative tasks are handled promptly and efficiently. By empowering individuals with the appropriate permissions, organizations can expedite processes and optimize their overall workflow management.
The importance of secure user permissions cannot be overstated in today’s digital landscape. By implementing robust permission structures, organizations can mitigate risks, safeguard sensitive data, and streamline their workflows. Customizable access rights ensure that each user has precisely the level of access they need, while also providing the flexibility to adapt to evolving organizational requirements. Ultimately, prioritizing secure user permissions is not just about protecting data—it’s about empowering organizations to operate efficiently and securely in an increasingly complex digital world.
To learn about Oneflow’s customizable user permissions, check out our other blog post here.